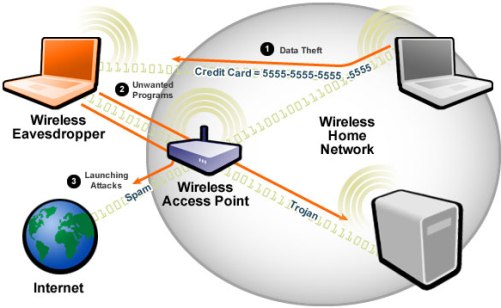
- Why Is Wireless Security Needed?
- Wireless technology is extending its reach from home
networks into the areas of education, medicine, government services, and
business establishments. Wireless networks add an extra level of security
complexity compared to wired networks. Whereas wired networks send their
signals through cable, wireless radio signals propogate through the air
and are naturally easier to intercept. Signals from most wireless LANs (WLAN)
pass through exterior walls and into nearby streets or parking lots.
These can be intercepted by anyone with any wireless computing device.
If security measures are hapazardly applied, the infrastructure and contents
of the wireless network are at the mercy of potentially malicious intruders
armed with a laptop and freely available sniffer utilities.
- Overview
- As we do a quick rewind in history, it is interesting to note that Wireless Networks have been around since 1971, starting with the ALOHA network. Close to that same time frame, the concepts behind the Ethernet protocol were also pioneered. Since those days, for the most part, the Ethernet frame used to encapsulate information so it could travel within the LAN has remained practically the same since it’s inception in the middle 60’s.
The Ethernet frame is practically the same when it travels over copper media regardless of the speed (10,100 or 1000Mb). We must note something very important: This frame in turn is encapsulated in a different container when it is going to be traveling over the WAN, or air as the media. Just picture this: To take pictures with your camera below the sea you must protect it (encapsulate it) with the proper apparel.
Up to this point, we have not mentioned anything about security. In those years the main objective was to share data and connect very small groups of people. To come up with an Ethernet network in those years, basically all that was needed was a coaxial cable and you could clamp on with the computer’s NIC to the cable. In those days, no attention was given to interweaving security into the Ethernet frame; the means for ensuring that information would be seen only by the recipient were never developed. In present time, to ensure interoperability of different types of equipment, the Ethernet frame is basically the same, but the security might be build around the frame, or the frame itself is encrypted as it travels on the media; and then it is unencrypted at the endpoint.
Let us look at one particular transmission media: the air. We see the same beginnings: wireless networks simply broadcast information. The encapsulation of the Ethernet frame was done in such a way just to ensure it could travel without damage or to be repaired to some extent when it was received in the other side. Later on this became fairly inconvenient, because anybody with the proper gear could just listen, and pick up the information and reconstruct whatever information was being sent over the air. All that followed in regards to wireless technologies as the years passed (WEP, WPA, VPNs) are the means to secure that frame as it travels in radio waves over the air, to ensure that the contents are not viewed by anybody else. All of the different security technologies have strengths and weaknesses, and the intention is to give an understanding of what can be achieved with each technology.
Moving fast forward on our history tape, the Ethernet frame later on began to carry another protocol, called TCP/IP. TCP/IP is now the protocol that carries the Internet world wide. TCP/IP is very versatile, because it can be encapsulated inside an Ethernet frame, Bluetooth protocol frames, or Wi-Fi frames, IPSec frames, etc.
Think about the last comment: VoIP is one of the fairly new types of data carried by the TCP/IP packet. You can have a phone number listed in San Antonio TX, and receive calls and dial from Mexico City, and all phone charges will be the same as if the person were actually living in San Antonio. With prices dropping for desktops and laptops, high-speed Internet access, and wireless hardware products, today's consumers enjoy the convenience of wireless access at home. They find the experience liberating and want this service to be available everywhere: in schools, the office and on the road.
- Businesses and higher education institutions have been responding to the demand. For example, business travelers can rely on most hotels to offer wireless connections, convention centers make them available to attendees and eating establishments offer them to their customers. Universities and colleges have wireless-equipped laptop requirements, and medical and nursing schools are requiring students to buy and use PDAs. Cities throughout the US are implementing Wi-Fi networks. Primarily targeted towards providing free or low cost access for citizens and tourists, some cities see it as an economic necessity. For example, the Corpus Christi, TX, Wi-Fi network is being implemented as part of an automated meter reading (AMR) capital improvement project.
- Security Issues
- The challenges of creating and maintaining a home wireless local area network (WLAN) pale in comparison with establishing the same in large office, campus, governmental, and metropolitan and settings. Security is a primary concern. The issues are multilayered and include:
- Acceptable use policy—the purpose of the network and associated devices; responsibility of the organization, IT department, and users
- Access control—who can access the network; whether guest service allowed;
- WLAN security standards for authentication and encryption—protecting access points; authorizing client to access point
- Detection and containment of rogue devices—detecting and containing laptops infected with malware; maintaining up-to-date anti-virus and anti-spyware definitions
- Intrusion prevention—implementing firewalls, network traffic sniffers and analysis programs
- Effective range or coverage—a home WLAN can reach upto 100 meters in radius; an enterprise WLAN can span several kilometers
Implementing multilayer WLAN security is not easy. While progress has been made developing security standards for wireless networks, administrators must constantly ensure that it is comprehensive, effective, and proactive.
- Relevance to Industry and Academia
- Because of their mission of teaching and learning, community colleges are a primary source of training the technical workforce in computer and networking technology. They play an important role in cybersecurity. Undergraduate programs strive to prepare students to deal with the real world by teaching them how to think critically, express themselves effectively in oral and written communications, and work together in teams. These life long skills will outlive the specific technical skills students acquire. On the other hand, organizations need people who have a good understanding of technology architecture, network ing protocols and systems. They simply lack the capacity to hire smart undergraduates into their IT departments and then train them.
The Global Wireless Education Consortium estimated that 300,000 workers with wireless knowledge were needed in 2005. According to JobBank USA, demand for computer security specialists will grow as businesses and government continue to invest in protecting their networks infrastructure from attack. Robert Half Technology, an IT recruiting firm, surveyed 1400 Chief Information Officers and found wireless networking to be a skill in demand. Thus a program such as this one where students are not only trained in the use of specific technical skills, but also acquire the knowledge of how information is used by organizations and the importance of protecting it, address both academic and business goals.
- Module Objectives
- Before starting this module, please determine your wireless networking needs. If your focus is to build a home network, or setup a network to handle up to 200 users, then this module is right for you. Topics to be covered include:
- Securing a wireless network by determining
- Internal risks
- External risks
- Preventing unauthorized access by
- Securing the Access Point (AP) itself
- Using Windows 2003 Server utilities
- Using Linux based solutions
- Securing data using
- Windows 2003 Server utilities
- Linux based solutions
- Examining security policies and procedures